
miércoles, 17 de noviembre de 2010
miércoles, 10 de noviembre de 2010
miércoles, 20 de octubre de 2010
lunes, 18 de octubre de 2010
miércoles, 6 de octubre de 2010
lunes, 27 de septiembre de 2010
miércoles, 22 de septiembre de 2010
miércoles, 8 de septiembre de 2010
miércoles, 1 de septiembre de 2010
Segundo algoritmo
Primer algoritmo
miércoles, 25 de agosto de 2010
lunes, 23 de agosto de 2010
ALGORITMOS EN YENKA
MATHEMATICS
YENKA 3D SHAPES:
an easy-to-use modelling tool for experimenting with 3D geometry, including nets, plans and elevations.
YENJA STATISTICS:
A powerful modelling tool for statistics and probability, using tools that include 3D games and a line-up of people.
YENKA COORDINATES:
Teach coordinate points using games on a set of 3D axes.
SCIENCE
YENKA INORGANIC CHEMISTRY:
A virtual chemistry laboratory where you can model reactions safely and easily, with over 100 chemicals to choose from.
YENKA ELECTROCHEMISTRY:
Experiment with electrolysis, electroplating and cells, using a range of electrocodes and solutions.
YENKA LIGHT AND SOUND:
Experiment with reflection, interference and diffraction in water, sound or EM waves, as well as modelling ray diagrams for optical systems.
YENKA MOTION:
Experiment freely with forces and motion, including friction, projectiles, oscillations and gravity.
YENKA ELECTRICITY AND MAGNETISM:
Simulate and design circuits safely and easily, choosing from wide variety of components.Experiment with electricity generation, transmission and use in full 3D.
YENKA ANALOGUE ELECTRONICS:
Experiment with analogue circuits including, resistors, capacitors, diodes, transistors, op amps and inputs and outputs.
YENKA DIGITAL ELECTRONICS:
Designs circuits with digital components including logic gates, couters, decoders and flip-flops.
TECHNOLOGY
YENKA BASIC CIRCUITS:
Create and simulates simple circuits using batteries, switches, LEDs, bulbs, resistors and other components.
YENKA ELECTRONICS:
Design and simulates circuits using over 150 types of component, testing and refining your design as your work.
TENCKA PCBs WITH ELECTRONICS:
An add.on for Yenka Electronics, with converts circuits into 3D PCB simulations, and exports for manufacture.
YENKA PICs:
write PIC and PICAXE routines using simple flowcharts, and test them on-screen, before using them to real chips.
YENKA GEARS:
Experiment with a range of mechanical components, such as gears, motors and flywheels, in full 3D.
Programación (YENKA)
YENKA 3D SHAPES:
an easy-to-use modelling tool for experimenting with 3D geometry, including nets, plans and elevations.
YENJA STATISTICS:
A powerful modelling tool for statistics and probability, using tools that include 3D games and a line-up of people.
YENKA COORDINATES:
Teach coordinate points using games on a set of 3D axes.
SCIENCE
YENKA INORGANIC CHEMISTRY:
A virtual chemistry laboratory where you can model reactions safely and easily, with over 100 chemicals to choose from.
YENKA ELECTROCHEMISTRY:
Experiment with electrolysis, electroplating and cells, using a range of electrocodes and solutions.
YENKA LIGHT AND SOUND:
Experiment with reflection, interference and diffraction in water, sound or EM waves, as well as modelling ray diagrams for optical systems.
YENKA MOTION:
Experiment freely with forces and motion, including friction, projectiles, oscillations and gravity.
YENKA ELECTRICITY AND MAGNETISM:
Simulate and design circuits safely and easily, choosing from wide variety of components.Experiment with electricity generation, transmission and use in full 3D.
YENKA ANALOGUE ELECTRONICS:
Experiment with analogue circuits including, resistors, capacitors, diodes, transistors, op amps and inputs and outputs.
YENKA DIGITAL ELECTRONICS:
Designs circuits with digital components including logic gates, couters, decoders and flip-flops.
TECHNOLOGY
YENKA BASIC CIRCUITS:
Create and simulates simple circuits using batteries, switches, LEDs, bulbs, resistors and other components.
YENKA ELECTRONICS:
Design and simulates circuits using over 150 types of component, testing and refining your design as your work.
TENCKA PCBs WITH ELECTRONICS:
An add.on for Yenka Electronics, with converts circuits into 3D PCB simulations, and exports for manufacture.
YENKA PICs:
write PIC and PICAXE routines using simple flowcharts, and test them on-screen, before using them to real chips.
YENKA GEARS:
Experiment with a range of mechanical components, such as gears, motors and flywheels, in full 3D.
Programación (YENKA)
miércoles, 18 de agosto de 2010
lunes, 16 de agosto de 2010
DIAGRAMA DE FLUJO

Es la representación grafica de un algoritmo.
Dados tres números determinar si la suma de una pareja de ellos es igual al tercer numero, si se cumple esta condición escribir iguales y en caso contrario escribir distintos.
3 9 6 iguales
3 + 6 = 9
2 3 4 distintos
2 + 4 = 6
algoritmo:
Pedir los tres valores.
Asignar el primer valor a A
Asignar el segundo valor a B
Asignar el tercer valor a C
Si A+B=C escribir "iguales" e ir a fin.
Si A+C=B escribir "iguales" e ir a fin.
Si B+C=A escribir "iguales" e ir a fin.
Escribir distintos e ir "diferentes"
miércoles, 11 de agosto de 2010
¿QUE ES UN ALGORITMO?
ALGORITMO
Es un método para resolver un problema mediante una serie de pasos definidos, precisos y finitos.
Preciso: implica el orden de realización de cada uno de los pasos
Definido: si se sigue dos veces, se obtiene el mismo resultado.
Finito: Tiene un numero determinado de pasos, implica que tiene un fin.
EJEMPLO:
Ingredientes:
(6 porciones)
½ taza de azúcar para hacer el caramelo
4 huevos
½ taza de agua
½ taza de azúcar esta es para el flan
1 2/3 de leche evaporada
2 cucharaditas de vainilla
Preparación:
En un molde para flan vacié la primera ½ taza de azúcar, colóquelo sobre el fuego y deje que se derrita el azúcar. Ladee el molde para que cubra bien el fondo y las paredes.
Aparte licue los huevos, la otra medita taza de azúcar, el agua, la leche evaporada y la vainilla. Vacíe sobre el caramelo.
Tape el molde con un trozo de papel aluminio y hornee a baño María durante 35 o 40 minutos.
Refrigere y desmolde.
Enseñando a un niño a atarse las agujetas
Asegurarse que cada hollo del tennis este ocupado por las agujetas.
Sostener cada ambos extremos de la agujeta con su mano correspondiente.
Doblar los extremos a la mitad en forma de ovalo, asegurarse que quede amplio.
Juntar los óvalos formados por los extremos, luego entrecruzamos. Aprietalos bien y listo!
Es un método para resolver un problema mediante una serie de pasos definidos, precisos y finitos.
Preciso: implica el orden de realización de cada uno de los pasos
Definido: si se sigue dos veces, se obtiene el mismo resultado.
Finito: Tiene un numero determinado de pasos, implica que tiene un fin.
EJEMPLO:
Ingredientes:
(6 porciones)
½ taza de azúcar para hacer el caramelo
4 huevos
½ taza de agua
½ taza de azúcar esta es para el flan
1 2/3 de leche evaporada
2 cucharaditas de vainilla
Preparación:
En un molde para flan vacié la primera ½ taza de azúcar, colóquelo sobre el fuego y deje que se derrita el azúcar. Ladee el molde para que cubra bien el fondo y las paredes.
Aparte licue los huevos, la otra medita taza de azúcar, el agua, la leche evaporada y la vainilla. Vacíe sobre el caramelo.
Tape el molde con un trozo de papel aluminio y hornee a baño María durante 35 o 40 minutos.
Refrigere y desmolde.
Enseñando a un niño a atarse las agujetas
Asegurarse que cada hollo del tennis este ocupado por las agujetas.
Sostener cada ambos extremos de la agujeta con su mano correspondiente.
Doblar los extremos a la mitad en forma de ovalo, asegurarse que quede amplio.
Juntar los óvalos formados por los extremos, luego entrecruzamos. Aprietalos bien y listo!
martes, 27 de abril de 2010
CAPITULO 8
Once the hacker gains access to the network, four types of threat may arise:
INFORMATION THEFT
breaking into a computer to obtain confidential information. Info can be used or sold for various purposes.Example:stealing a organization´s proprietary info, such as research and development info.
DATA LOSS AND MANIPULATION
breaking into a computer to destroy or alter data records.Examples of date loss:sending a virus that reformats a computer´s hard drive. Examples of data manipulation:breaking into a records system to change information, such as the price of an item.
IDENTITY THEFT
a form of info theft where personal info is stolen for the purpose of taking over someone´s identity. Using this info an individual can obtain legal documents, apply for credit and make unauthorized online purchases.Identity theft is a growing problem costing billions of dollars per year.
DISRUPTION OF SERVICE
preventing legitimate users from accessing services to which they should be entitled.

External Threats
arise from individuals working outside of an organization. They do not have authorized access to the computer systems or network.
Internal threats
occur when someone has authorized access to the network through a user account or have physical access to the network equipment.
SOCIAL ENGINEERING
Techniques uesd by an attacker to manipulate ussuspecting people into providing info or computer system access.
techiniques:
PRETEXTING
fraudulent acquisition of sensitive info, primarily over the telephone, where an invented scenario persuades a target of legitimacy.
PHISHING
fraudulent acquisition os sensitive info through the impersonation of a trustworthy source.
VISHING
fraudulent aquisition of sensitive info through VoIP that terminates in a computer.
VIRUSes
It needs to be activated. Once activated, a virus may do nothing more than replicate itself and spread.A more serious virus may be programmed to delete or corrupt specific files before spreading. Viruses can be transmitted via email attachments, downloaded files, instant messages or via diskette, CD or USB devices.
Worms
Uses the network to send copies of itself to any connected hosts.Do not necessarily require activation or human intervention.
Trojan Horses
is a non-self replicating program that is written to appear like a legitimate program, when in fact it is an attack tool.It may be relatively harmless or can contain code that can damage the contents of the computer's hard drive.Can also create a back door into a system allowing hackers to gain access.

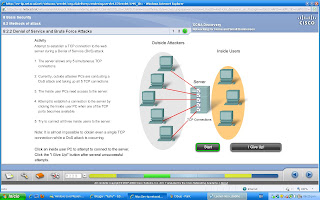
Denial of Service (DoS)
Attacks on an individual computer or groups of computers with the intent to deny services to intended users. DoS attacks can target end user systems, servers, routers, and network links.
In general, DoS attacks seek to:
Flood a system or network with traffic to prevent legitimate network traffic from flowing
Disrupt connections between a client and server to prevent access to a service
Types of Dos attacks:
SYN (synchronous) Flooding: a flood of packets are sent to a server requesting a client connection. The packets contain invalid source IP addresses. The server becomes occupied trying to respond to these fake requests and therefore cannot respond to legitimate ones.
Ping of death: a packet that is greater in size than the maximum allowed by IP (65,535 bytes) is sent to a device. This can cause the receiving system to crash.
DDoS
It is designed to saturate and overwhelm network links with useless data.Operates on a much larger scale than DoS attacks.The attack points may be unsuspecting computers that have been previously infected by the DDoS code.The systems that are infected with the DDoS code attack the target site when invoked.
Brute force attack
Is another type of attack.
A fast computer is used to try to guess passwords or to decipher an encryption code. The attacker tries a large number of possibilities in rapid succession to gain access or crack the code. Brute force attacks can cause a denial of service due to excessive traffic to a specific resource or by locking out user accounts.
SPYWARE
a malicious program, typically installed without a user's knowledge, designed to perform tasks such as capture keystrokes, for the benefit of the originator of the program.
POPUP
a form of online advertising to increase web traffic or capture e-mail addresses that displays when a user opens certain websites or clicks on specific links.
COOKIES
are a form of spyware. They are used to record information about an Internet user when they visit websites.May be useful or desirable by allowing personalization and other time saving techniques. Many web sites require that cookies be enabled in order to allow the user to connect.
ADWARE
is a form of spyware used to collect information about a user based on websites the user visits.Is commonly installed by a user in exchange for a "free" product. When a user opens a browser window, Adware can start new browser instances which attempt to advertize products or services based on a user's surfing practices. The unwanted browser windows can open repeatedly, and can make surfing the Internet very difficult, especially with slow Internet connections.
SPAM
unsolicited or junk e-mail messages sent to multiple recipients for either legitimate or fraudulent purposes.
SECURITY TOOLS
Firewall
controls traffic to and from a network.
Spam filter
software installed on an end-user workstation or server to identify and remove unwanted emails.
Patches and Updates
software applied to an OS or application to correct a known security vulnerability or add functionality.
Anti-spyware
to detect and remove spyware and adware.
Popup blocker
to prevent popups and unders.
Anti-virus
to detect and remove viruses, worms and Trojan.
Some of the signs that a virus, worm or Trojan horse may be present include:
Computer starts acting abnormally
Program does not respond to mouse and keystrokes
Programs starting or shutting down on their own
Email program begins sending out large quantities of email
CPU usage is very high
There are unidentifiable, or a large number of processes running
Computer slows down significantly or crashes
Features that can be included in Anti-virus programs are:
Email checking - Scans incoming and outgoing emails, and identifies suspicious attachments.
Resident dynamic scanning - Checks executable files and documents when they are accessed.
Scheduled scans - Virus scans can be scheduled to run at regular intervals and check specific drives or the entire computer.
Automatic Updates - Checks for, and downloads, known virus characteristics and patterns. Can be scheduled to check for updates on a regular basis.
Actions to prevent the spread of spam include:
Apply OS and application updates when available.
Run an Antivirus program regularly and keep it up to date.
Do not forward suspect emails.
Do not open email attachments, especially from people you do not know.
Set up rules in your email to delete spam that by-pass the anti-spam software.
Identify sources of spam and report it to a network administrator so it can be blocked.
Report incidents to the governmental agency that deals with abuse by spam.
A Firewall is one of the most effective security tools available for protecting internal network users from external threats.Controls the traffic between them as well as helps prevent unauthorized access. Firewall techniques
Packet Filtering - Prevents or allows access based on IP or MAC addresses.
Application Filtering - Prevents or allows access to specific application types based on port numbers.
URL Filtering - Prevents or allows access to websites based on specific URLs or keywords.
Stateful Packet Inspection (SPI) - Unsolicited packets are blocked unless permitted specifically. SPI can also include the capability to recognize and filter out specific types of attacks such as DoS.
Firewall products come packaged in various forms:
Appliance-based firewalls -is built-in to a dedicated hardware device known as a security appliance.
Server-based firewalls -consists of a firewall application that runs on a network operating system (NOS) such as UNIX, Windows or Novell.
Integrated Firewalls -implemented by adding firewall functionality to an existing device, such as a router.
Personal firewalls -reside on host computers and are not designed for LAN implementations. They may be available by default from the OS or may be installed from an outside vendor.
USING A FIREWALL


ONE FIREWALL CONFIG
external network
internal network
DMZ.
To monitor the traffic and determine what traffic should be passed to the DMZ,internally, and what should be denied altogether.
TWO FIREWALL CONFIG
There is an internal and external firewall with the DMZ located between them.
A two-firewall configuration is more appropriate for larger, more complex networks that handle a lot more traffic.
INFORMATION THEFT
breaking into a computer to obtain confidential information. Info can be used or sold for various purposes.Example:stealing a organization´s proprietary info, such as research and development info.
DATA LOSS AND MANIPULATION
breaking into a computer to destroy or alter data records.Examples of date loss:sending a virus that reformats a computer´s hard drive. Examples of data manipulation:breaking into a records system to change information, such as the price of an item.
IDENTITY THEFT
a form of info theft where personal info is stolen for the purpose of taking over someone´s identity. Using this info an individual can obtain legal documents, apply for credit and make unauthorized online purchases.Identity theft is a growing problem costing billions of dollars per year.
DISRUPTION OF SERVICE
preventing legitimate users from accessing services to which they should be entitled.

External Threats
arise from individuals working outside of an organization. They do not have authorized access to the computer systems or network.
Internal threats
occur when someone has authorized access to the network through a user account or have physical access to the network equipment.
SOCIAL ENGINEERING
Techniques uesd by an attacker to manipulate ussuspecting people into providing info or computer system access.
techiniques:
PRETEXTING
fraudulent acquisition of sensitive info, primarily over the telephone, where an invented scenario persuades a target of legitimacy.
PHISHING
fraudulent acquisition os sensitive info through the impersonation of a trustworthy source.
VISHING
fraudulent aquisition of sensitive info through VoIP that terminates in a computer.
VIRUSes
It needs to be activated. Once activated, a virus may do nothing more than replicate itself and spread.A more serious virus may be programmed to delete or corrupt specific files before spreading. Viruses can be transmitted via email attachments, downloaded files, instant messages or via diskette, CD or USB devices.
Worms
Uses the network to send copies of itself to any connected hosts.Do not necessarily require activation or human intervention.
Trojan Horses
is a non-self replicating program that is written to appear like a legitimate program, when in fact it is an attack tool.It may be relatively harmless or can contain code that can damage the contents of the computer's hard drive.Can also create a back door into a system allowing hackers to gain access.

Denial of Service (DoS)
Attacks on an individual computer or groups of computers with the intent to deny services to intended users. DoS attacks can target end user systems, servers, routers, and network links.
In general, DoS attacks seek to:
Flood a system or network with traffic to prevent legitimate network traffic from flowing
Disrupt connections between a client and server to prevent access to a service
Types of Dos attacks:
SYN (synchronous) Flooding: a flood of packets are sent to a server requesting a client connection. The packets contain invalid source IP addresses. The server becomes occupied trying to respond to these fake requests and therefore cannot respond to legitimate ones.
Ping of death: a packet that is greater in size than the maximum allowed by IP (65,535 bytes) is sent to a device. This can cause the receiving system to crash.
DDoS
It is designed to saturate and overwhelm network links with useless data.Operates on a much larger scale than DoS attacks.The attack points may be unsuspecting computers that have been previously infected by the DDoS code.The systems that are infected with the DDoS code attack the target site when invoked.
Brute force attack
Is another type of attack.
A fast computer is used to try to guess passwords or to decipher an encryption code. The attacker tries a large number of possibilities in rapid succession to gain access or crack the code. Brute force attacks can cause a denial of service due to excessive traffic to a specific resource or by locking out user accounts.

SPYWARE
a malicious program, typically installed without a user's knowledge, designed to perform tasks such as capture keystrokes, for the benefit of the originator of the program.
POPUP
a form of online advertising to increase web traffic or capture e-mail addresses that displays when a user opens certain websites or clicks on specific links.
COOKIES
are a form of spyware. They are used to record information about an Internet user when they visit websites.May be useful or desirable by allowing personalization and other time saving techniques. Many web sites require that cookies be enabled in order to allow the user to connect.
ADWARE
is a form of spyware used to collect information about a user based on websites the user visits.Is commonly installed by a user in exchange for a "free" product. When a user opens a browser window, Adware can start new browser instances which attempt to advertize products or services based on a user's surfing practices. The unwanted browser windows can open repeatedly, and can make surfing the Internet very difficult, especially with slow Internet connections.
SPAM
unsolicited or junk e-mail messages sent to multiple recipients for either legitimate or fraudulent purposes.
SECURITY TOOLS
Firewall
controls traffic to and from a network.
Spam filter
software installed on an end-user workstation or server to identify and remove unwanted emails.
Patches and Updates
software applied to an OS or application to correct a known security vulnerability or add functionality.
Anti-spyware
to detect and remove spyware and adware.
Popup blocker
to prevent popups and unders.
Anti-virus
to detect and remove viruses, worms and Trojan.
Some of the signs that a virus, worm or Trojan horse may be present include:
Computer starts acting abnormally
Program does not respond to mouse and keystrokes
Programs starting or shutting down on their own
Email program begins sending out large quantities of email
CPU usage is very high
There are unidentifiable, or a large number of processes running
Computer slows down significantly or crashes
Features that can be included in Anti-virus programs are:
Email checking - Scans incoming and outgoing emails, and identifies suspicious attachments.
Resident dynamic scanning - Checks executable files and documents when they are accessed.
Scheduled scans - Virus scans can be scheduled to run at regular intervals and check specific drives or the entire computer.
Automatic Updates - Checks for, and downloads, known virus characteristics and patterns. Can be scheduled to check for updates on a regular basis.
Actions to prevent the spread of spam include:
Apply OS and application updates when available.
Run an Antivirus program regularly and keep it up to date.
Do not forward suspect emails.
Do not open email attachments, especially from people you do not know.
Set up rules in your email to delete spam that by-pass the anti-spam software.
Identify sources of spam and report it to a network administrator so it can be blocked.
Report incidents to the governmental agency that deals with abuse by spam.
A Firewall is one of the most effective security tools available for protecting internal network users from external threats.Controls the traffic between them as well as helps prevent unauthorized access. Firewall techniques
Packet Filtering - Prevents or allows access based on IP or MAC addresses.
Application Filtering - Prevents or allows access to specific application types based on port numbers.
URL Filtering - Prevents or allows access to websites based on specific URLs or keywords.
Stateful Packet Inspection (SPI) - Unsolicited packets are blocked unless permitted specifically. SPI can also include the capability to recognize and filter out specific types of attacks such as DoS.
Firewall products come packaged in various forms:
Appliance-based firewalls -is built-in to a dedicated hardware device known as a security appliance.
Server-based firewalls -consists of a firewall application that runs on a network operating system (NOS) such as UNIX, Windows or Novell.
Integrated Firewalls -implemented by adding firewall functionality to an existing device, such as a router.
Personal firewalls -reside on host computers and are not designed for LAN implementations. They may be available by default from the OS or may be installed from an outside vendor.
USING A FIREWALL


ONE FIREWALL CONFIG
external network
internal network
DMZ.
To monitor the traffic and determine what traffic should be passed to the DMZ,internally, and what should be denied altogether.
TWO FIREWALL CONFIG
There is an internal and external firewall with the DMZ located between them.
A two-firewall configuration is more appropriate for larger, more complex networks that handle a lot more traffic.
martes, 20 de abril de 2010
viernes, 16 de abril de 2010
INFOGRAMA
La infografía es una representación más visual que la propia de los textos, en la que intervienen descripciones, narraciones o interpretaciones, presentadas de manera gráfica normalmente figurativa, que pueden o no coincidir con grafismos abstractos y/o sonidos. La infografía nació como un medio de trasmitir información gráficamente. Los mapas, gráficos, viñetas, etc. son infogramas, es decir unidades menores de la infografía, con la que se presenta una información completa aunque pueda ser complementaria o de sintesis.
Hay ciertos elementos básicos que se deben tomar en cuenta al diseñar una infografía, como lo son:
La proporción:
es el recorrido de un plano en movimiento que se convierte en un volumen. Debe ser correcta y tener cuidado al agrandar una forma porque puede quedar distorsionada. Es decir, la imagen tiene que ser extendida en sus dos dimensiones (alto y ancho) proporcionalmente.
La perspectiva:
nos ayuda a representar la realidad y crear efectos volumétricos. Puede un gráfico ser más atractivo cunado se aplica este elemento básico del diseño .Se debe ser cuidadoso con ella, respetando las respectivas medidas que se le otorga. A pesar de vivir en un mundo tridimensional, la bidimensionalidad se entiende mejor en la página impresa.
Las texturas:
consisten en la modificación o variación de la superficie de los materiales utilizados, ya sea de una forma visual o táctil. En los diseños, si no se utilizan bien pueden causar confusiones o ilusiones ópticas.
Las formas:
hablamos de forma cuando el trazo de línea se une en un mismo punto. Sus características son estáticas o dinámicas dependiendo del uso que se les de.
Las formas más básicas del diseño son: el círculo, el rectángulo y el triángulo.
El plano:
permite fragmentar y dividir el espacio, de esta forma podemos delimitar y clasificar las diferentes zonas de nuestra composición.
El movimiento:
es uno de los elementos visuales que implica y dota de más fuerza a un gráfico. Una fotografía capta con mayor facilidad este elemento. Pero en un dibujo, el diseñador debe buscar los elementos necesarios como líneas rectas, sombras, curvas, repetición, etc. para lograr el efecto.
El color:
es uno de los elementos fundamentales y más evidentes del diseño y que puede dar carácter y significado a las imágenes que se les aplica. En las artes gráficas tenemos dos grandes categorías con respecto al color que son: imagen a color e imagen en blanco y negro.
Paratexto:
El término paratexto designa al conjunto de los enunciados que rodean a un texto: el título, subtítulos, prefacio, indicación de insertar, índice de materias, etc. El paratexto está destinado a hacer presente el texto, asegurar su presencia en el mundo, Se distingue el paratexto de autor y el paratexto editorial. El primero es producido por el autor (su nombre, epígrafe, prefacio, dedicatoria, nota al pie de página) y el segundo al editor (tapa, catálogo, copyright, etc.).
mi infografia sera de HAIR MYHTS
Hay ciertos elementos básicos que se deben tomar en cuenta al diseñar una infografía, como lo son:
La proporción:
es el recorrido de un plano en movimiento que se convierte en un volumen. Debe ser correcta y tener cuidado al agrandar una forma porque puede quedar distorsionada. Es decir, la imagen tiene que ser extendida en sus dos dimensiones (alto y ancho) proporcionalmente.
La perspectiva:
nos ayuda a representar la realidad y crear efectos volumétricos. Puede un gráfico ser más atractivo cunado se aplica este elemento básico del diseño .Se debe ser cuidadoso con ella, respetando las respectivas medidas que se le otorga. A pesar de vivir en un mundo tridimensional, la bidimensionalidad se entiende mejor en la página impresa.
Las texturas:
consisten en la modificación o variación de la superficie de los materiales utilizados, ya sea de una forma visual o táctil. En los diseños, si no se utilizan bien pueden causar confusiones o ilusiones ópticas.
Las formas:
hablamos de forma cuando el trazo de línea se une en un mismo punto. Sus características son estáticas o dinámicas dependiendo del uso que se les de.
Las formas más básicas del diseño son: el círculo, el rectángulo y el triángulo.
El plano:
permite fragmentar y dividir el espacio, de esta forma podemos delimitar y clasificar las diferentes zonas de nuestra composición.
El movimiento:
es uno de los elementos visuales que implica y dota de más fuerza a un gráfico. Una fotografía capta con mayor facilidad este elemento. Pero en un dibujo, el diseñador debe buscar los elementos necesarios como líneas rectas, sombras, curvas, repetición, etc. para lograr el efecto.
El color:
es uno de los elementos fundamentales y más evidentes del diseño y que puede dar carácter y significado a las imágenes que se les aplica. En las artes gráficas tenemos dos grandes categorías con respecto al color que son: imagen a color e imagen en blanco y negro.
Paratexto:
El término paratexto designa al conjunto de los enunciados que rodean a un texto: el título, subtítulos, prefacio, indicación de insertar, índice de materias, etc. El paratexto está destinado a hacer presente el texto, asegurar su presencia en el mundo, Se distingue el paratexto de autor y el paratexto editorial. El primero es producido por el autor (su nombre, epígrafe, prefacio, dedicatoria, nota al pie de página) y el segundo al editor (tapa, catálogo, copyright, etc.).
mi infografia sera de HAIR MYHTS
miércoles, 14 de abril de 2010
Capitulo 7
GLOSSARY
RF:
radio frequency. electromagnetic waves generated by AC and sent to an antenna within the electromagnetic spectrum.
IrDA:
infrared data association. defines protocol standards for the short range exchange of data over infrared light for uses such as PANs.
ISM:
industrial, scientifical and medical bands. Radio bands defined by the ITU-R in 5.150of the Radio Regulations and share with license-free, erro-tolerant communications applications such as wireless LANs and Bluetooth.
Bluetooth:
Wireless industry standard that uses an unlicensed radio frequency for short-range communication enabling portable devices to communicate over chort distances.
WLAN:
wireless local area network. Two or more computers or devices equipped to use spread-spectyrum technology based on radio waves for communication within a limited area.
encryption:
The application of the specific algorithm so as to alter the appearence of the data making it incomprehensive to those who are not authorized to see the information.
authentication:
Aprocess implemeted on a netwotk to verify the identify of a user.
troughput:
The rate at which a computer or network sends or receives data meassured in bits per second(bps).
wireless client:
Any host device that can connect to a wireless network.
STA:
Abbreviation for STAtion, a basic network device.
SSID:
service set identifier. The code assigned to a packet that designates that the communication is part of a wireless network.
IBSS:
independent basic service set. an 802.11 network comprised of a collection os stations that communicate with each other, but not with a network infrastructure.
BSS:
basic service set. A group of 802.11 devices connected to an access point.
ESS:
extended service set. A colection of BSSs that communicate with one another through the distribution system (usually the wired Ethernet port on an access point).
CSMA/CA:
carrier sense multiple access with collision avoidance.The basic medium access for 802.11 wireless network.
RTS:
request to send. Along with clear to send, is used by the 802.11 wireless networking protocl to reduce frame collision introduced by hidden terminal problem and exposed node problem.
CTS:
clear to send.Along with request to send, is used by the 802.11 wireless networking protocol to reduce frame collisions introduced by the hidden terminal problem and exposed node problem.
ACK:
Acknowledgement. A transmission control character(or a transmission frame) that confirms a transmitted message was received un corrupted without errors or that receiving station is ready to accept transmissions.
MAC filtering:
Access control method that permits and denies network access based on MAC addresses ti specific devices through the use of blacklists and whitelists.
open aithentication:
A type of wireless authentication where any and all clients are able to associate regardless of who they are.
PSK:
pre-shared key. A secret shared between the wireless AP and a client to control access on a network.
EAP:
Extends Authentication Protocol. An authentication framework, not a specific autjentiction mechanism. Most commonly used in wireless LANs, EAP provides common functions and a negociation of the desired authentication mechanism.
RADIUS:
remote authentication dial in user service.An AAA(authentication, authorization, and accounting) protocol used for security applications, such as network access or IP mobility. It authenticates users and machines in both local and remote aituations.
WEP:
Wired Equivalent Privacy. Part of the IEEE 802.11 wireless networking standard that provides a low level of security.
WPA: Wi-Fi Protected Access. Developed to adress security issues in WEP. Provides higher level of security in a wireless network.
firmware:
Software embedded in a hardware device typically provided on flash ROMs or as a binary image file that can be uploaded onto existing hardware by a user.
site survey:
Software installed servers and desktop computers that provides threat protection capabilities.
DIFERENT STANDRDS
802.11a
Uses 5 GHz RF spectrum
Not compatible with 2.4 GHz spectrum, i.e. 802.11 b/g/n devices
Range is approximately 33% that of the 802.11 b/g
Relatively expensive to implement compared to other technologies
Increasingly difficult to find 802.11a compliant equipment
802.11b
First of the 2.4 GHz technologies
Maximum data-rate of 11 Mbps
Range of approximately 46 m (150 ft) indoors/96 m (300 ft) outdoors
802.11g
2.4 GHz technologies
Maximum data-rate increase to 54 Mbps
Same range as the 802.11b
Backwards compatible with 802.11b
802.11n
Newest standard in development
2.4 GHz technologies (draft standard specifies support for 5 GHz)
Extends the range and data throughput
Backwards compatible with existing 802.11g and 802.11b equipment (draft standard specifies 802.11a support)
ANTENNAS:
Used on APs and Wireless bridges
Increases the output signal strength from a wireless device
Receives wireless signals from other devices such as STAs
Increase in signal strength from an antenna is known as the gain
Higher gains usually translate into increased transmission distances.
CLIENT:
also known as a STA
a mobile device that can participate in the wireless LAN
AP:
converts Ethernet Frame type to 802.11 format
controls acces by wireless clients into the wired LAN.
BRIDGE:
allows range wireless communication.
RF:
radio frequency. electromagnetic waves generated by AC and sent to an antenna within the electromagnetic spectrum.
IrDA:
infrared data association. defines protocol standards for the short range exchange of data over infrared light for uses such as PANs.
ISM:
industrial, scientifical and medical bands. Radio bands defined by the ITU-R in 5.150of the Radio Regulations and share with license-free, erro-tolerant communications applications such as wireless LANs and Bluetooth.
Bluetooth:
Wireless industry standard that uses an unlicensed radio frequency for short-range communication enabling portable devices to communicate over chort distances.
WLAN:
wireless local area network. Two or more computers or devices equipped to use spread-spectyrum technology based on radio waves for communication within a limited area.
encryption:
The application of the specific algorithm so as to alter the appearence of the data making it incomprehensive to those who are not authorized to see the information.
authentication:
Aprocess implemeted on a netwotk to verify the identify of a user.
troughput:
The rate at which a computer or network sends or receives data meassured in bits per second(bps).
wireless client:
Any host device that can connect to a wireless network.
STA:
Abbreviation for STAtion, a basic network device.
SSID:
service set identifier. The code assigned to a packet that designates that the communication is part of a wireless network.
IBSS:
independent basic service set. an 802.11 network comprised of a collection os stations that communicate with each other, but not with a network infrastructure.
BSS:
basic service set. A group of 802.11 devices connected to an access point.
ESS:
extended service set. A colection of BSSs that communicate with one another through the distribution system (usually the wired Ethernet port on an access point).
CSMA/CA:
carrier sense multiple access with collision avoidance.The basic medium access for 802.11 wireless network.
RTS:
request to send. Along with clear to send, is used by the 802.11 wireless networking protocl to reduce frame collision introduced by hidden terminal problem and exposed node problem.
CTS:
clear to send.Along with request to send, is used by the 802.11 wireless networking protocol to reduce frame collisions introduced by the hidden terminal problem and exposed node problem.
ACK:
Acknowledgement. A transmission control character(or a transmission frame) that confirms a transmitted message was received un corrupted without errors or that receiving station is ready to accept transmissions.
MAC filtering:
Access control method that permits and denies network access based on MAC addresses ti specific devices through the use of blacklists and whitelists.
open aithentication:
A type of wireless authentication where any and all clients are able to associate regardless of who they are.
PSK:
pre-shared key. A secret shared between the wireless AP and a client to control access on a network.
EAP:
Extends Authentication Protocol. An authentication framework, not a specific autjentiction mechanism. Most commonly used in wireless LANs, EAP provides common functions and a negociation of the desired authentication mechanism.
RADIUS:
remote authentication dial in user service.An AAA(authentication, authorization, and accounting) protocol used for security applications, such as network access or IP mobility. It authenticates users and machines in both local and remote aituations.
WEP:
Wired Equivalent Privacy. Part of the IEEE 802.11 wireless networking standard that provides a low level of security.
WPA: Wi-Fi Protected Access. Developed to adress security issues in WEP. Provides higher level of security in a wireless network.
firmware:
Software embedded in a hardware device typically provided on flash ROMs or as a binary image file that can be uploaded onto existing hardware by a user.
site survey:
Software installed servers and desktop computers that provides threat protection capabilities.
DIFERENT STANDRDS
802.11a
Uses 5 GHz RF spectrum
Not compatible with 2.4 GHz spectrum, i.e. 802.11 b/g/n devices
Range is approximately 33% that of the 802.11 b/g
Relatively expensive to implement compared to other technologies
Increasingly difficult to find 802.11a compliant equipment
802.11b
First of the 2.4 GHz technologies
Maximum data-rate of 11 Mbps
Range of approximately 46 m (150 ft) indoors/96 m (300 ft) outdoors
802.11g
2.4 GHz technologies
Maximum data-rate increase to 54 Mbps
Same range as the 802.11b
Backwards compatible with 802.11b
802.11n
Newest standard in development
2.4 GHz technologies (draft standard specifies support for 5 GHz)
Extends the range and data throughput
Backwards compatible with existing 802.11g and 802.11b equipment (draft standard specifies 802.11a support)
ANTENNAS:
Used on APs and Wireless bridges
Increases the output signal strength from a wireless device
Receives wireless signals from other devices such as STAs
Increase in signal strength from an antenna is known as the gain
Higher gains usually translate into increased transmission distances.
CLIENT:
also known as a STA
a mobile device that can participate in the wireless LAN
AP:
converts Ethernet Frame type to 802.11 format
controls acces by wireless clients into the wired LAN.
BRIDGE:
allows range wireless communication.
domingo, 14 de marzo de 2010
CHAPTER 6
A web server and a web client use specific protocols and standards in the process of exchanging information to ensure that the messages are received and understood. These protocols cover: application, transport, Internetwork and network access protocols.
Application Protocol
Hypertext Transfer Protocol (HTTP) governs the way that a web server and a web client interact. HTTP defines the format of the requests and responses exchanged between the client and server. HTTP relies on other protocols to govern how the messages are transported between client and server.
Transport Protocol
Transmission Control Protocol (TCP) is the transport protocol that manages the individual conversations between web servers and web clients. TCP formats the HTTP messages into segments to be sent to the destination host. It also provides flow control and acknowledgement of packets exchanged between hosts.
Internetwork Protocol
The most common internetwork protocol is Internet Protocol (IP). IP is responsible for taking the formatted segments from TCP, assigning the logical addressing, and encapsulating them into packets for routing to the destination host.
Network Access Protocols
Network access protocols perform two primary functions:
Data link management protocols take the packets from IP and encapsulate them into the appropriate frame format for the local network. These protocols assign the physical addresses to the frames and prepare them to be transmitted over the network.
The standards and protocols for the physical media govern how the bits are represented on the media, how the signals are sent over the media, and how they are interpreted by the receiving hosts. Network interface cards implement the appropriate protocols for the media that is being used.
TCP
When an application requires acknowledgment that a message is delivered, it uses TCP.
TCP breaks up a message into small pieces known as segments. The segments are numbered in sequence and passed to IP process for assembly into packets. TCP keeps track of the number of segments that have been sent to a specific host from a specific application. If the sender does not receive an acknowledgement within a certain period of time, it assumes that the segments were lost and retransmits them. Only the portion of the message that is lost is resent, not the entire message.
On the receiving host, TCP is responsible for reassembling the message segments and passing them to the application.
FTP and HTTP are examples of applications that use TCP to ensure delivery of data.
The TCP slows down information transfer. In those cases, UDP may be a more appropriate transport protocol.
UDP is a 'best effort' delivery system that does not require acknowledgment of receipt.It is not guaranteed that the letter is received, but the chances are good.
UDP is preferable with applications such as streaming audio, video and voice over IP (VoIP).
An example of an application that uses UDP is Internet radio. If some of the message is lost during its journey over the network, it is not retransmitted. If a few packets are missed, the listener might hear a slight break in the sound. If TCP were used and the lost packets were resent, the transmission would pause to receive them and the disruption would be more noticeable.
PORTS
Is used to keep track of specific conversations and destination services requested. Every message that a host sends contains both a source and destination port.
Destination Port
The client places a destination port number in the segment to tell the destination server what service is being requested.
Source Port
This allows multiple conversations to occur simultaneously. In other words, multiple devices can request HTTP service from a web server at the same time. The separate conversations are tracked based on the source ports.
SOCKET
is used to identify the server and service being requested by the client
Domain Name System (DNS)
Provides a way for hosts to use this name to request the IP address of a specific server. DNS names are registered and organized on the Internet within specific high level groups, or domains. Some of the most common high level domains on the Internet are .com, .edu, and .net.
When the DNS server receives the request, it checks its table to determine the IP address associated with that web server. If the local DNS server does not have an entry for the requested name, it queries another DNS server within the domain. When the DNS server learns the IP address, that information is sent back to the client. If the DNS server cannot determine the IP address, the request will time out and the client will not be able to communicate with the web server.
When a web client receives the IP address of a web server, the client browser uses that IP address and port 80 to request web services. This request is sent to the server using the Hypertext Transfer Protocol (HTTP).
The information content of a web page is encoded using specialized 'mark-up' languages. HTML (Hypertext Mark-up Language) is the most commonly used but others, such as XML and XHTML, are gaining popularity.
The HTTP protocol is not a secure protocol; information could easily be intercepted by other users as it is sent over the network.
The File Transfer Protocol (FTP)
Provides an easy method to transfer files from one computer to another.
FTP server enables a client to
Exchange files between devices
manage files remotely by sending file management commands such as delete or rename It uses two different ports to communicate between client and server
To begin an FTP session it uses port 21. Once the session is opened, the server will change to port 20 to transfer the data files.
EMAILS
Various application protocols used in processing email include SMTP, POP3, IMAP4.
Simple Mail Transfer Protocol (SMTP)
Used by an email client to send messages to its local email server. The local server then decides if the message is destined for a local mailbox or if the message is addressed to a mailbox on another server.
SMTP requests are sent to port 25.
Post Office Protocol (POP3)
A server that supports POP clients receives and stores messages addressed to its users. When the client connects to the email server, the messages are downloaded to the client.Messages are not kept on the server after they have been accessed by the client. Clients contact POP3 servers on port 110.
Internet Message Access Protocol (IMAP4)
It does the same that POP3, but IMAP keeps the messages unless its users errase them.
It requests on port 143.
The following are typical entries when configuring an email client:
POP3 or IMAP4 Server name
SMTP Server name
Username
User password
SPAM and Virus filters
A call to a regular telephone (land line or cell phone) requires the use of a gateway to access the Public Switched Telephone Network (PSTN).
PORTS
Help servers to know which service is being requested by a client.
Are assigned and managed by the Internet Corporation for Assigned Names and Numbers (ICANN).
Well-Known Ports
Destination ports that are associated with common network applications. These ports are in the range of 1 to 1023.
Registered Ports
Ports 1024 through 49151 can be used as either source or destination ports. These can be used by organizations to register specific applications such as IM applications.
Private Ports
Ports 49152 through 65535, often used as source ports. These ports can be used by any application.
layered model
Depicts the operation of the protocols occurring within each layer, as well as the interaction with the layers above and below it.
Benefits:
*Assists in protocol design.
*Fosters competition because products from different vendors can work together.
*Prevents technology or capability changes in one layer from affecting other layers above and and below.
*Fosters competition because products from different vendors can work together.
*Prevents technology or capability changes in one layer from affecting other layers above and below.
*Provides a common language to describe networking functions and capabilities.
TCP/IP MODEL
It specify the interaction of each protocol
OSI MODEL
Includes all functions, or tasks, associated with Inter-network communications, not just those related to the TCP/IP protocols. Compared to the TCP/IP model, which only has four layers, the OSI model organizes the tasks into seven more specific groups. A task, or group of tasks, is then assigned to each of the seven OSI layers.
APPLICATION LAYER:
define interfaces between application software and network communication functions.
provides standardized services such as file transfer between systems.
PRESENTATION LAYER:
standardizes user data formats for use between different types of systems.
encodes and decodes user data; encrypts and decrypts data; compresses and and decompresses data.
SESSION LAYER:
manages user sessions and dialogues.
mantains logical links between systems.
TRANSPORT LAYER:
manages end-to-end message delivery over the network.
can provide reliable and sequential packet delivery through error recovery and flow control mechanisms.
NETWORK LAYER:
routes packets according to unique network devices addresses.
DATA LINK LAYER:
defines procedures for operating the communications links.
detects and corrects frame transmit errors.
PHYSICAL LAYER:
defines physcial means of sending data over network devices.
interfaces between network medium and devices.
defines optical, electrical and mechanical characteristics.
The Packet Tracer (PT)allows viewing of simulated data being transmitted between two hosts. It uses Protocol Data Units (PDUs) to represent network traffic frames and displays protocol stack information at the appropriate layers of the OSI model.
Layer 1 (Physical): Fast Ethernet port
Layer 2 (Data Link): Ethernet Mac addresses
Layer 3 (Network): IP addresses
Layer 4 (Transport): TCP port numbers
Application Protocol
Hypertext Transfer Protocol (HTTP) governs the way that a web server and a web client interact. HTTP defines the format of the requests and responses exchanged between the client and server. HTTP relies on other protocols to govern how the messages are transported between client and server.
Transport Protocol
Transmission Control Protocol (TCP) is the transport protocol that manages the individual conversations between web servers and web clients. TCP formats the HTTP messages into segments to be sent to the destination host. It also provides flow control and acknowledgement of packets exchanged between hosts.
Internetwork Protocol
The most common internetwork protocol is Internet Protocol (IP). IP is responsible for taking the formatted segments from TCP, assigning the logical addressing, and encapsulating them into packets for routing to the destination host.
Network Access Protocols
Network access protocols perform two primary functions:
Data link management protocols take the packets from IP and encapsulate them into the appropriate frame format for the local network. These protocols assign the physical addresses to the frames and prepare them to be transmitted over the network.
The standards and protocols for the physical media govern how the bits are represented on the media, how the signals are sent over the media, and how they are interpreted by the receiving hosts. Network interface cards implement the appropriate protocols for the media that is being used.
TCP
When an application requires acknowledgment that a message is delivered, it uses TCP.
TCP breaks up a message into small pieces known as segments. The segments are numbered in sequence and passed to IP process for assembly into packets. TCP keeps track of the number of segments that have been sent to a specific host from a specific application. If the sender does not receive an acknowledgement within a certain period of time, it assumes that the segments were lost and retransmits them. Only the portion of the message that is lost is resent, not the entire message.
On the receiving host, TCP is responsible for reassembling the message segments and passing them to the application.
FTP and HTTP are examples of applications that use TCP to ensure delivery of data.
The TCP slows down information transfer. In those cases, UDP may be a more appropriate transport protocol.
UDP is a 'best effort' delivery system that does not require acknowledgment of receipt.It is not guaranteed that the letter is received, but the chances are good.
UDP is preferable with applications such as streaming audio, video and voice over IP (VoIP).
An example of an application that uses UDP is Internet radio. If some of the message is lost during its journey over the network, it is not retransmitted. If a few packets are missed, the listener might hear a slight break in the sound. If TCP were used and the lost packets were resent, the transmission would pause to receive them and the disruption would be more noticeable.
PORTS
Is used to keep track of specific conversations and destination services requested. Every message that a host sends contains both a source and destination port.
Destination Port
The client places a destination port number in the segment to tell the destination server what service is being requested.
Source Port
This allows multiple conversations to occur simultaneously. In other words, multiple devices can request HTTP service from a web server at the same time. The separate conversations are tracked based on the source ports.
SOCKET
is used to identify the server and service being requested by the client
Domain Name System (DNS)
Provides a way for hosts to use this name to request the IP address of a specific server. DNS names are registered and organized on the Internet within specific high level groups, or domains. Some of the most common high level domains on the Internet are .com, .edu, and .net.
When the DNS server receives the request, it checks its table to determine the IP address associated with that web server. If the local DNS server does not have an entry for the requested name, it queries another DNS server within the domain. When the DNS server learns the IP address, that information is sent back to the client. If the DNS server cannot determine the IP address, the request will time out and the client will not be able to communicate with the web server.
When a web client receives the IP address of a web server, the client browser uses that IP address and port 80 to request web services. This request is sent to the server using the Hypertext Transfer Protocol (HTTP).
The information content of a web page is encoded using specialized 'mark-up' languages. HTML (Hypertext Mark-up Language) is the most commonly used but others, such as XML and XHTML, are gaining popularity.
The HTTP protocol is not a secure protocol; information could easily be intercepted by other users as it is sent over the network.
The File Transfer Protocol (FTP)
Provides an easy method to transfer files from one computer to another.
FTP server enables a client to
Exchange files between devices
manage files remotely by sending file management commands such as delete or rename It uses two different ports to communicate between client and server
To begin an FTP session it uses port 21. Once the session is opened, the server will change to port 20 to transfer the data files.
EMAILS
Various application protocols used in processing email include SMTP, POP3, IMAP4.
Simple Mail Transfer Protocol (SMTP)
Used by an email client to send messages to its local email server. The local server then decides if the message is destined for a local mailbox or if the message is addressed to a mailbox on another server.
SMTP requests are sent to port 25.
Post Office Protocol (POP3)
A server that supports POP clients receives and stores messages addressed to its users. When the client connects to the email server, the messages are downloaded to the client.Messages are not kept on the server after they have been accessed by the client. Clients contact POP3 servers on port 110.
Internet Message Access Protocol (IMAP4)
It does the same that POP3, but IMAP keeps the messages unless its users errase them.
It requests on port 143.
The following are typical entries when configuring an email client:
POP3 or IMAP4 Server name
SMTP Server name
Username
User password
SPAM and Virus filters
A call to a regular telephone (land line or cell phone) requires the use of a gateway to access the Public Switched Telephone Network (PSTN).
PORTS
Help servers to know which service is being requested by a client.
Are assigned and managed by the Internet Corporation for Assigned Names and Numbers (ICANN).
Well-Known Ports
Destination ports that are associated with common network applications. These ports are in the range of 1 to 1023.
Registered Ports
Ports 1024 through 49151 can be used as either source or destination ports. These can be used by organizations to register specific applications such as IM applications.
Private Ports
Ports 49152 through 65535, often used as source ports. These ports can be used by any application.
layered model
Depicts the operation of the protocols occurring within each layer, as well as the interaction with the layers above and below it.
Benefits:
*Assists in protocol design.
*Fosters competition because products from different vendors can work together.
*Prevents technology or capability changes in one layer from affecting other layers above and and below.
*Fosters competition because products from different vendors can work together.
*Prevents technology or capability changes in one layer from affecting other layers above and below.
*Provides a common language to describe networking functions and capabilities.
TCP/IP MODEL
It specify the interaction of each protocol
OSI MODEL
Includes all functions, or tasks, associated with Inter-network communications, not just those related to the TCP/IP protocols. Compared to the TCP/IP model, which only has four layers, the OSI model organizes the tasks into seven more specific groups. A task, or group of tasks, is then assigned to each of the seven OSI layers.
APPLICATION LAYER:
define interfaces between application software and network communication functions.
provides standardized services such as file transfer between systems.
PRESENTATION LAYER:
standardizes user data formats for use between different types of systems.
encodes and decodes user data; encrypts and decrypts data; compresses and and decompresses data.
SESSION LAYER:
manages user sessions and dialogues.
mantains logical links between systems.
TRANSPORT LAYER:
manages end-to-end message delivery over the network.
can provide reliable and sequential packet delivery through error recovery and flow control mechanisms.
NETWORK LAYER:
routes packets according to unique network devices addresses.
DATA LINK LAYER:
defines procedures for operating the communications links.
detects and corrects frame transmit errors.
PHYSICAL LAYER:
defines physcial means of sending data over network devices.
interfaces between network medium and devices.
defines optical, electrical and mechanical characteristics.
The Packet Tracer (PT)allows viewing of simulated data being transmitted between two hosts. It uses Protocol Data Units (PDUs) to represent network traffic frames and displays protocol stack information at the appropriate layers of the OSI model.
Layer 1 (Physical): Fast Ethernet port
Layer 2 (Data Link): Ethernet Mac addresses
Layer 3 (Network): IP addresses
Layer 4 (Transport): TCP port numbers
CHAPTER 5
A host needs an IP address to participate on the Internet.
IP address
Is a logical network address that identifies a particular host. It must be properly configured and unique in order to communicate with other devices on the Internet.
Is assigned to the Network interface connection for a host.
This connection is usually a network interface card (NIC) installed in the device.
Examples:
workstations, servers, network printers and IP phones.
Some servers can have more than one NIC and each of these has its own IP address.
Router interfaces that provide connections to an IP network will also have an IP address.
Is simply a series of 32 binary bits (ones and zeros)
The 32 bits are grouped into four 8-bit bytes called octets.
The 32-bit IP address is defined with IP version 4 (IPv4) and is currently the most common form of IP address on the Internet.
If all 8 bits are 1s, 11111111 the value of the octet is 255 (128+64+32+16+8+4+2+1).
If the 8 bits are mixed, such as the example
Hierarchical addressing
The logical 32-bit IP address is made up of two parts. The first part identifies the network and the second part identifies a host on that network. Both parts are required in an IP address.
Routers only need to know how to reach each network.
subnet mask
signifies which part of the IP address is network and which part is host.
The 1s in the subnet mask represent the network; the 0s represent the host.
When a host sends a packet, it compares its subnet mask to its own IP address and the destination IP address. If the network bits match, both the source and destination host are on the same network and the packet can be delivered locally.
IP addresses classes
Classes A, B and C are commercial addresses and are assigned to hosts. Class D is reserved for multicast use and Class E is for experimental use.
Class C addresses have three octets for the network portion and one for the hosts. Usually assigned to small networks.
Class B addresses have two octets to represent the network portion and two for the hosts. Typically used for medium-sized networks.
Class A addresses have only one octet to represent the network portion and three to represent the hosts. Typically assigned to large organizations.
Unique public IP address
All hosts that connect directly to the Internet needs it.There is a risk of running out of IP addresses.
One solution to this problem was to reserve some private addresses for use exclusively inside an organization. This allows hosts within an organization to communicate with one another without the need of a unique public IP address.
RFC 1918
Is a standard that reserves several ranges of addresses within each of the classes A, B and C.
Private addressesAre not routed on the Internet
The use of private addresses can provide a measure of security since they are only visible on the local network.
Loopback addressThere are also private Addresses that can be used for the diagnostic testing of devices.
The class A, 127.0.0.0 network, is reserved for it.
we also categorize IP addresses as
UNICAST
For a unicast packet to be sent and received, a destination IP address must be in the IP packet header. A corresponding destination MAC address must also be present in the Ethernet frame header. The IP address and MAC address combine to deliver data to one specific destination host.
BROADCAST
This means that all hosts on that local network (broadcast domain) will receive and look at the packet. Many network protocols, such as ARP and DHCP use broadcasts.
A broadcast IP address for a network needs a corresponding broadcast MAC address in the Ethernet frame.
MULTICAST
As with a unicast or broadcast address, multicast IP addresses need a corresponding multicast MAC address to actually deliver frames on a local network. The multicast MAC address is a special value that begins with 01-00-5E in hexadecimal. The value ends by converting the lower 23 bits of the IP multicast group address into the remaining 6 hexadecimal characters of the Ethernet address.
IP addresses can be assigned either statically or dynamically
STATIC
With a static assignment, the network administrator must manually configure the network information for a host.
This includes:
the host IP address, subnet mask and default gateway.
Advantages:
Useful for printers, servers and other networking devices that need to be accessible to clients on the network.
If hosts normally access a server at a particular IP address, it would not be good if that address changed.
Provide increased control of network resources, but it can be time consuming to enter the information on each host. Therefore, errors are more likely to occur.
It is important to maintain an accurate list of which IP addresses are assigned to which devices.These are permanent addresses and are not normally reused.
DYNAMIC
On local networks it is often the case that the user population changes frequently. New users arrive with laptops and need a connection. Others have new workstations that need to be connected. Rather than have the network administrator assign IP addresses for each workstation, it is easier to have IP addresses assigned automatically. This is done using a protocol known as Dynamic Host Configuration Protocol (DHCP).
DHCP provides a mechanism for the automatic assignment of addressing information such as IP address, subnet mask, default gateway, and other configuration information.
Benefit of DHCP:
an address is not permanently assigned to a host but is only leased for a period of time.
The router provides a GATEWAY through which hosts on one network can communicate with hosts on different networks. Each interface on a router is connected to a separate network.
Every host on a network must use the router as a gateway to other networks. Therefore, each host must know the IP address of the router interface connected to the network where the host is attached. This address is known as the default gateway address It can be either statically configured on the host, or received dynamically by DHCP.
When an integrated router is configured as a DHCP server, it provides its own internal IP address as the default gateway to DHCP clients. It also provides them with their respective IP address and subnet mask.
The integrated router acts as a DHCP server for all local hosts attached to it, either by Ethernet cable or wirelessly.The default IP address configured on the local integrated router interface is usually a private Class C address.
When an integrated router is connected to the ISP, it acts like a DHCP client to receive the correct external network IP address for the Internet interface. ISPs usually provide an Internet-routable address, which enables hosts connected to the integrated router to have access to the Internet.
WAYS OF CONNECTING A HOST
Direct Connection
Some customers have just a single computer with a direct connection from the ISP through a modem. In this case, the public address from the ISP DHCP server is assigned to the single host.
Connection Through an Integrated Router
When there is more than one host that needs access to the Internet, the ISP modem can be attached directly to an integrated router instead of directly to a single computer. This enables the creation of a home or small business network. The integrated router receives the public address from the ISP. Internal hosts receive private addresses from the integrated router.
Connection Through a Gateway Device
Gateway devices combine an integrated router and a modem in one unit, and connect directly to the ISP service. As with integrated routers, the gateway device receives a public address from the ISP and internal PCs will receive private addresses from the gateway device.
TRANSLATION NAT
The integrated router is able to translate many internal IP addresses to the same public address, by using it.Only packets destined for other networks need to be translated.
IP address
Is a logical network address that identifies a particular host. It must be properly configured and unique in order to communicate with other devices on the Internet.
Is assigned to the Network interface connection for a host.
This connection is usually a network interface card (NIC) installed in the device.
Examples:
workstations, servers, network printers and IP phones.
Some servers can have more than one NIC and each of these has its own IP address.
Router interfaces that provide connections to an IP network will also have an IP address.
Is simply a series of 32 binary bits (ones and zeros)
The 32 bits are grouped into four 8-bit bytes called octets.
The 32-bit IP address is defined with IP version 4 (IPv4) and is currently the most common form of IP address on the Internet.
If all 8 bits are 1s, 11111111 the value of the octet is 255 (128+64+32+16+8+4+2+1).
If the 8 bits are mixed, such as the example
Hierarchical addressing
The logical 32-bit IP address is made up of two parts. The first part identifies the network and the second part identifies a host on that network. Both parts are required in an IP address.
Routers only need to know how to reach each network.
subnet mask
signifies which part of the IP address is network and which part is host.
The 1s in the subnet mask represent the network; the 0s represent the host.
When a host sends a packet, it compares its subnet mask to its own IP address and the destination IP address. If the network bits match, both the source and destination host are on the same network and the packet can be delivered locally.
IP addresses classes
Classes A, B and C are commercial addresses and are assigned to hosts. Class D is reserved for multicast use and Class E is for experimental use.
Class C addresses have three octets for the network portion and one for the hosts. Usually assigned to small networks.
Class B addresses have two octets to represent the network portion and two for the hosts. Typically used for medium-sized networks.
Class A addresses have only one octet to represent the network portion and three to represent the hosts. Typically assigned to large organizations.
Unique public IP address
All hosts that connect directly to the Internet needs it.There is a risk of running out of IP addresses.
One solution to this problem was to reserve some private addresses for use exclusively inside an organization. This allows hosts within an organization to communicate with one another without the need of a unique public IP address.
RFC 1918
Is a standard that reserves several ranges of addresses within each of the classes A, B and C.
Private addressesAre not routed on the Internet
The use of private addresses can provide a measure of security since they are only visible on the local network.
Loopback addressThere are also private Addresses that can be used for the diagnostic testing of devices.
The class A, 127.0.0.0 network, is reserved for it.
we also categorize IP addresses as
UNICAST
For a unicast packet to be sent and received, a destination IP address must be in the IP packet header. A corresponding destination MAC address must also be present in the Ethernet frame header. The IP address and MAC address combine to deliver data to one specific destination host.
BROADCAST
This means that all hosts on that local network (broadcast domain) will receive and look at the packet. Many network protocols, such as ARP and DHCP use broadcasts.
A broadcast IP address for a network needs a corresponding broadcast MAC address in the Ethernet frame.
MULTICAST
As with a unicast or broadcast address, multicast IP addresses need a corresponding multicast MAC address to actually deliver frames on a local network. The multicast MAC address is a special value that begins with 01-00-5E in hexadecimal. The value ends by converting the lower 23 bits of the IP multicast group address into the remaining 6 hexadecimal characters of the Ethernet address.
IP addresses can be assigned either statically or dynamically
STATIC
With a static assignment, the network administrator must manually configure the network information for a host.
This includes:
the host IP address, subnet mask and default gateway.
Advantages:
Useful for printers, servers and other networking devices that need to be accessible to clients on the network.
If hosts normally access a server at a particular IP address, it would not be good if that address changed.
Provide increased control of network resources, but it can be time consuming to enter the information on each host. Therefore, errors are more likely to occur.
It is important to maintain an accurate list of which IP addresses are assigned to which devices.These are permanent addresses and are not normally reused.
DYNAMIC
On local networks it is often the case that the user population changes frequently. New users arrive with laptops and need a connection. Others have new workstations that need to be connected. Rather than have the network administrator assign IP addresses for each workstation, it is easier to have IP addresses assigned automatically. This is done using a protocol known as Dynamic Host Configuration Protocol (DHCP).
DHCP provides a mechanism for the automatic assignment of addressing information such as IP address, subnet mask, default gateway, and other configuration information.
Benefit of DHCP:
an address is not permanently assigned to a host but is only leased for a period of time.
The router provides a GATEWAY through which hosts on one network can communicate with hosts on different networks. Each interface on a router is connected to a separate network.
Every host on a network must use the router as a gateway to other networks. Therefore, each host must know the IP address of the router interface connected to the network where the host is attached. This address is known as the default gateway address It can be either statically configured on the host, or received dynamically by DHCP.
When an integrated router is configured as a DHCP server, it provides its own internal IP address as the default gateway to DHCP clients. It also provides them with their respective IP address and subnet mask.
The integrated router acts as a DHCP server for all local hosts attached to it, either by Ethernet cable or wirelessly.The default IP address configured on the local integrated router interface is usually a private Class C address.
When an integrated router is connected to the ISP, it acts like a DHCP client to receive the correct external network IP address for the Internet interface. ISPs usually provide an Internet-routable address, which enables hosts connected to the integrated router to have access to the Internet.
WAYS OF CONNECTING A HOST
Direct Connection
Some customers have just a single computer with a direct connection from the ISP through a modem. In this case, the public address from the ISP DHCP server is assigned to the single host.
Connection Through an Integrated Router
When there is more than one host that needs access to the Internet, the ISP modem can be attached directly to an integrated router instead of directly to a single computer. This enables the creation of a home or small business network. The integrated router receives the public address from the ISP. Internal hosts receive private addresses from the integrated router.
Connection Through a Gateway Device
Gateway devices combine an integrated router and a modem in one unit, and connect directly to the ISP service. As with integrated routers, the gateway device receives a public address from the ISP and internal PCs will receive private addresses from the gateway device.
TRANSLATION NAT
The integrated router is able to translate many internal IP addresses to the same public address, by using it.Only packets destined for other networks need to be translated.
viernes, 5 de marzo de 2010
apunte quark xpress: capas
Las capas son componentes para documentos de diseño
cada uno de los elementos que integran nuestro trabajo. en quark xpress una capa o layer se define como una rebanada de lay out que contiene elementos especificos, cada capa puede ocultarse, bloquearse, traer al frente o enviar hacia atras, imprimir o borrar. la ventaja de usar capas es el poder manipular cada una de las partes de un trabajo por separado, para asi no modificar o alterar algun otro elemento.
Menu color
existen diversos tipos o bases de colores con los cuales podemos crear fotolitos o colores, entre ellos estan:
cmyk: tinta de colores estandar utilizando en el proceso de impresion a 4 colores. Tambien llamado tinta de procesos. El proceso de impresion a 4 colores utiliza la combinacion cmyk sobrepuesta para lograr un efecto deseado al contrario, el spot color utiliza solamente una tinta para su impresion.
los colores websafe se utilizan para el diseño de paginas web, los cuales estan en un formato exadecimal y tienen una basa rgp(rojo verde azul) que es un modelo de color con el cual se obtiene un tono diferente a partir de la suma de distintas cantidades de los tres colores primarios. Es el modelo mas utilizado para visualizar y trabajar con imagenes digitales en una pantalla
Calibracion de color
su finalidad es medir o ajustar la respuesta del color de un dispositivo, para establcer un modelo del color estandar
cada uno de los elementos que integran nuestro trabajo. en quark xpress una capa o layer se define como una rebanada de lay out que contiene elementos especificos, cada capa puede ocultarse, bloquearse, traer al frente o enviar hacia atras, imprimir o borrar. la ventaja de usar capas es el poder manipular cada una de las partes de un trabajo por separado, para asi no modificar o alterar algun otro elemento.
Menu color
existen diversos tipos o bases de colores con los cuales podemos crear fotolitos o colores, entre ellos estan:
cmyk: tinta de colores estandar utilizando en el proceso de impresion a 4 colores. Tambien llamado tinta de procesos. El proceso de impresion a 4 colores utiliza la combinacion cmyk sobrepuesta para lograr un efecto deseado al contrario, el spot color utiliza solamente una tinta para su impresion.
los colores websafe se utilizan para el diseño de paginas web, los cuales estan en un formato exadecimal y tienen una basa rgp(rojo verde azul) que es un modelo de color con el cual se obtiene un tono diferente a partir de la suma de distintas cantidades de los tres colores primarios. Es el modelo mas utilizado para visualizar y trabajar con imagenes digitales en una pantalla
Calibracion de color
su finalidad es medir o ajustar la respuesta del color de un dispositivo, para establcer un modelo del color estandar
miércoles, 10 de febrero de 2010
CHAPTER 3
NETWORKS
Networks provide the ability to connect people and equipment no matter where they are in the world.
VOICE NETWORK COMPUTER NETWORK VIDEO NETWORK
The Internet is considered a "network of networks" because it is literally made up of thousands of networks that are connected to each other.
Here are other uses of a network and the Internet:
Sharing music and video files
Research and on-line learning
Chatting with friends
Planning vacations
Purchasing gifts and supplies
CATEGORIES:
PERIPHERALS
it doesnt communicate directly on the network. instead,it relies on its connected host to perform all network operations.
cameras, sacnners, and local attached prinetrs.
HOSTS
send and receive user traffic.it has an IP network address.
personal computers and network attached printers.
NETWORK DEVICES
connect other devices, mainly hosts. these devices move and control network traffic.
hubs,swithces and routers.
NETWORK MEDIA
provides connections between hosts and network devices. it can be wired, such as copper and fiber optic or use wireless technologies.
COMPUTER ROLE IN NETWORK
ALL CONNECTED TO THE SWITCH
file access client/ file server
store the file, the client accesses with client sofware such as windows explorer.
web server/ browser client
runs server software and cleints use their browser software, such as Windows internet to access web pages.
email server/ email client
runs server software and clients use their mail client software, such as microsoft outlook to access.
PEER-TO-PEER NETWORKS
many computers function as the servers and clients on the network. This type of network is called a peer-to-peer network.
ADVANTAGES:
easy to set up
less complexity
lower cost
can be used for simpel tasks, such as transferring files and sharing printers.
DISADVANTAGES:
no centralized administration
not as secure
not scalable
all devices may act both clients and servers which can slow their performance.
NETWORK TOPOLOGIES
When networks are installed
PSYSICAL TOPOLOGY MAP
created to record where each host is located and how it is connected to the network.
shows where the wiring is installed and the locations of the networking devices that connect the hosts.
LOGYCAL TOPOLOGY MAP
groups hosts by how they use the network
Host names, addresses, group information and applications can be recorded on it.
SURCE, CHANNEL and DESTINATION
MESSAGE SIGNAL SIGNAL MESSAGE
MESSAGE----TRANSMITTER-----TRANSMISSION MEDIUM-----RECEIVER----MESSAGE DESTINATION
RULES OF COMMUNICATION
Message format
Message size
Timing
Encapsulation
Encoding
Standard message pattern
MESSAGE ENCODING
emite una idea------la cuenta a otro------el otro por fin se imagina la idea contada
SOURCE ENCODED--------------------DESTINATION DECODED
MESSAGE FORMATTINGH
DESTINATION: physcial hardware address
SOURCE: physcial hardware address
START FLAG: start of message indicator
RECIPIENT: destination identifier
SENDER: source indentifier
ENCAPSULATED: data bits
END OF FRAME: end of message indicator
MESSAGE SIZE
Too short or long messages cant be delivered,they need to be divided in small pieces.
MESSAGE TIMING
Access Method
Hosts on a network need an access method to know when to begin sending messages and how to respond when errors occur.
Flow control
Source and destination hosts use flow control to negotiate correct timing for successful communication.
Response Timeout
Hosts on the network also have rules that specify how long to wait for responses and what action to take if a response timeout occurs.
MESSAGE PATTERNS
UNICAST: A one-to-one message pattern
MULTICAST: When a host needs to send messages using a one-to-many pattern,
BROADCAST: If all hosts on the network need to receive the message at the same time
Protocols
In a wired environment, a local network is defined as an area where all hosts must "speak the same language" or in computer terms "share a common protocol".
SATANDARIZATION OF PROTOCOLS
Standards are beneficial to networking in many ways:
Facilitate design
Simplify product development
Promote competition
Provide consistent interconnections
Facilitate training
Provide more vendor choices for customers
Ethernet, has become more common than the others. It has become a de facto standard.
PHYSICAL ADDRESSING
Every Ethernet network interface has a physical address assigned to it when it is manufactured. This address is known as the Media Access Control (MAC) Address. The MAC address identifies each source and destination host on the network.
ETHERNET COMUNICATION
The format for Ethernet frames specifies the location of the destination and source MAC addresses, and additional information including:
Preamble for sequencing and timing
Start of frame delimiter
Length and type of frame
Frame check sequence to detect transmission errors
HIERACHICAL DESIGN OF ETHERNET
In networking, hierarchical design is used to group devices into multiple networks that are organized in a layered approach.
It has three basic layers:
Access Layer - to provide connections to hosts in a local Ethernet network.
Distribution Layer - to interconnect the smaller local networks.
Core Layer - a high-speed connection between distribution layer devices.
LOGYCAL ADDRESSING
The IP address is known as a logical address because it is assigned logically based on where the host is located.
The IP address, or network address, is assigned to each host by a network administrator based on the local network.
SWITHCES
An Ethernet switch is a device that is used at the Access Layer. Like a hub, a switch connects multiple hosts to the network. A switch can forward a message to a specific host. When a host sends a message to another host on the switch, the switch accepts and decodes the frames to read the physical (MAC) address portion of the message.
Networks provide the ability to connect people and equipment no matter where they are in the world.
VOICE NETWORK COMPUTER NETWORK VIDEO NETWORK
The Internet is considered a "network of networks" because it is literally made up of thousands of networks that are connected to each other.
Here are other uses of a network and the Internet:
Sharing music and video files
Research and on-line learning
Chatting with friends
Planning vacations
Purchasing gifts and supplies
CATEGORIES:
PERIPHERALS
it doesnt communicate directly on the network. instead,it relies on its connected host to perform all network operations.
cameras, sacnners, and local attached prinetrs.
HOSTS
send and receive user traffic.it has an IP network address.
personal computers and network attached printers.
NETWORK DEVICES
connect other devices, mainly hosts. these devices move and control network traffic.
hubs,swithces and routers.
NETWORK MEDIA
provides connections between hosts and network devices. it can be wired, such as copper and fiber optic or use wireless technologies.
COMPUTER ROLE IN NETWORK
ALL CONNECTED TO THE SWITCH
file access client/ file server
store the file, the client accesses with client sofware such as windows explorer.
web server/ browser client
runs server software and cleints use their browser software, such as Windows internet to access web pages.
email server/ email client
runs server software and clients use their mail client software, such as microsoft outlook to access.
PEER-TO-PEER NETWORKS
many computers function as the servers and clients on the network. This type of network is called a peer-to-peer network.
ADVANTAGES:
easy to set up
less complexity
lower cost
can be used for simpel tasks, such as transferring files and sharing printers.
DISADVANTAGES:
no centralized administration
not as secure
not scalable
all devices may act both clients and servers which can slow their performance.
NETWORK TOPOLOGIES
When networks are installed
PSYSICAL TOPOLOGY MAP
created to record where each host is located and how it is connected to the network.
shows where the wiring is installed and the locations of the networking devices that connect the hosts.
LOGYCAL TOPOLOGY MAP
groups hosts by how they use the network
Host names, addresses, group information and applications can be recorded on it.
SURCE, CHANNEL and DESTINATION
MESSAGE SIGNAL SIGNAL MESSAGE
MESSAGE----TRANSMITTER-----TRANSMISSION MEDIUM-----RECEIVER----MESSAGE DESTINATION
RULES OF COMMUNICATION
Message format
Message size
Timing
Encapsulation
Encoding
Standard message pattern
MESSAGE ENCODING
emite una idea------la cuenta a otro------el otro por fin se imagina la idea contada
SOURCE ENCODED--------------------DESTINATION DECODED
MESSAGE FORMATTINGH
DESTINATION: physcial hardware address
SOURCE: physcial hardware address
START FLAG: start of message indicator
RECIPIENT: destination identifier
SENDER: source indentifier
ENCAPSULATED: data bits
END OF FRAME: end of message indicator
MESSAGE SIZE
Too short or long messages cant be delivered,they need to be divided in small pieces.
MESSAGE TIMING
Access Method
Hosts on a network need an access method to know when to begin sending messages and how to respond when errors occur.
Flow control
Source and destination hosts use flow control to negotiate correct timing for successful communication.
Response Timeout
Hosts on the network also have rules that specify how long to wait for responses and what action to take if a response timeout occurs.
MESSAGE PATTERNS
UNICAST: A one-to-one message pattern
MULTICAST: When a host needs to send messages using a one-to-many pattern,
BROADCAST: If all hosts on the network need to receive the message at the same time
Protocols
In a wired environment, a local network is defined as an area where all hosts must "speak the same language" or in computer terms "share a common protocol".
SATANDARIZATION OF PROTOCOLS
Standards are beneficial to networking in many ways:
Facilitate design
Simplify product development
Promote competition
Provide consistent interconnections
Facilitate training
Provide more vendor choices for customers
Ethernet, has become more common than the others. It has become a de facto standard.
PHYSICAL ADDRESSING
Every Ethernet network interface has a physical address assigned to it when it is manufactured. This address is known as the Media Access Control (MAC) Address. The MAC address identifies each source and destination host on the network.
ETHERNET COMUNICATION
The format for Ethernet frames specifies the location of the destination and source MAC addresses, and additional information including:
Preamble for sequencing and timing
Start of frame delimiter
Length and type of frame
Frame check sequence to detect transmission errors
HIERACHICAL DESIGN OF ETHERNET
In networking, hierarchical design is used to group devices into multiple networks that are organized in a layered approach.
It has three basic layers:
Access Layer - to provide connections to hosts in a local Ethernet network.
Distribution Layer - to interconnect the smaller local networks.
Core Layer - a high-speed connection between distribution layer devices.
LOGYCAL ADDRESSING
The IP address is known as a logical address because it is assigned logically based on where the host is located.
The IP address, or network address, is assigned to each host by a network administrator based on the local network.
SWITHCES
An Ethernet switch is a device that is used at the Access Layer. Like a hub, a switch connects multiple hosts to the network. A switch can forward a message to a specific host. When a host sends a message to another host on the switch, the switch accepts and decodes the frames to read the physical (MAC) address portion of the message.
domingo, 7 de febrero de 2010
CHAPTER 2 resume
To perform a specific task, a special type of computer program, known as an operating system (OS)is required,which controls input and output functions.
In addition, the entered data is manipulated inside of the computer, stored in RAM and processed by the CPU. This internal manipulation and processing is also controlled by the OS. All computerized devices, such as servers, desktops, laptops or handhelds, require an OS in order to function.
PURPOSE OF AN OPERATING SYSTEM
A user interacts with the computer system through an application, such as
word processor
spreadsheet
computer game or instant messaging program
Application programs are designed for a specific purpose, such as word processing, and know nothing of the underlying electronics.
The portion of the OS code that interacts directly with the computer hardware is known as the kernel
The portion that interfaces with the applications and user, is known as the shell
The CLI, the user interacts directly with the system in a text-based environment by entering commands on the keyboard at a command prompt.
The GUI interface allows the user to interact with the system in an environment that uses graphical images, multimedia, and text.
REDIRECTOR
To work with resources that are not directly connected to the computer system, a special piece of software must be added that allows a device to send and receive data from the network.
May either be an integral part of the OS or may need to be installed separately as a network client. When installed, the operating system becomes a network operating system (NOS).
OPERATING SYSTEM REQUIERMENTS
These resources are specified by the manufacturer and include such things as:
Amount of RAM
Hard disk space required
Processor type and speed
Video resolution
Choosing an appropriate OS requires many factors to be considered before deciding which one to use in a given environment.
SECURITY
SUPPORT
POLITICS
COST
AVAILABILITY
RESOURCES
PLATFROM
USE
Types of OS:
Microsoft Windows: XP, Vista, 2003 Server
UNIX-Based: IBM AIX, Hewlett Packard HPUX, and Sun Solaris
BSD - Free BSD
Linux-Based (Many varieties)
Macintosh OS X
Non-Unix Proprietary: IBM OS/400, z/OS
There are several operating systems released under a different type of licensing scheme known as the GNU Public License (GPL).
Windows XP, Mac OS X and UNIX are all examples of commercial OS software.
OS selection
determine the user requiermentes
determine choices and OS
technicaland financial resources available
other restrictions
implement selected OS
OS installation Methods:
CLEAN INSTALL
is done on a new system or in cases where no upgrade path exists between the current OS and the one being installed.
UPGRADE
With an upgrade, system configuration settings, applications and data are preserved. It simply replaces the old OS files with the new OS files.
MULTI-BOOT
It is possible to install more than one OS on a computer to create a multi-boot system.
VIRTUALIZATION
It enables multiple copies of an OS to be run on a single set of hardware, thus creating many virtual machines.
PREPARING OS FOR INSTALLATION
A pre-installation checklist helps ensure that the installation process is successful.
1. Verify that all hardware is certified to work with the selected OS.
2. Verify that the hardware resources meet or exceed the published minimum requirements.
3. Confirm that the appropriate installation medium is available. Due to the file size of current operating systems, they are usually available on both CD and DVD medium.
4. If the OS is to be installed on a system that already contains data: (a) Use system diagnostic tools and utilities to ensure the current OS installation is in good condition, free of malicious or damaging files and codes; (b) Complete a full backup of all important files.
5. If performing a clean-install, verify that all application software is available for installation.
BEFORE IT
One of the techniques available to help protect data is to divide the hard drive into multiple partitions
it's also necessary to determine the type of file system to use.
CONFIFURING FOR A NETWORK
3 parts to the IP configuration, which must be correct for the computer to send and receive information:
IP address - identifies the computer on the network.
Subnet mask - is used to identify the network on which the computer is connected.
Default gateway - identifies the device that the computer uses to access the Internet or another network.
COMPUTER NIC default gateway IP INTERNET
MANUAL IP CONF
network adm.
DYNAMIC IP CONF
server---------- ip adress----------subnet mask-------def gateway-----host
computer naming
A computer name provides a user friendly name, making it easier for users to connect to shared resources such as folders and printers on other computers.
NETWORK NAME AND ADDRESS PLANNING helps them to find you in case.
PATCHES
A patch is a piece of program code that can correct a problem or enhance the functionality of an application program or OS.
Patches to operating systems can be installed in different ways, depending on the OS and the needs of the user. Options for downloading and installing updates include:
Automatic installation
a computer automatically accesses a manufacture'sweb site bightly to check for any OS updates to install.
Prompt for Permission
the suer is available to decide not to install it based on reports of poor computer performance after installation.
Manual
to correct known functionality and security issues within and operating system
In addition, the entered data is manipulated inside of the computer, stored in RAM and processed by the CPU. This internal manipulation and processing is also controlled by the OS. All computerized devices, such as servers, desktops, laptops or handhelds, require an OS in order to function.
PURPOSE OF AN OPERATING SYSTEM
A user interacts with the computer system through an application, such as
word processor
spreadsheet
computer game or instant messaging program
Application programs are designed for a specific purpose, such as word processing, and know nothing of the underlying electronics.
The portion of the OS code that interacts directly with the computer hardware is known as the kernel
The portion that interfaces with the applications and user, is known as the shell
The CLI, the user interacts directly with the system in a text-based environment by entering commands on the keyboard at a command prompt.
The GUI interface allows the user to interact with the system in an environment that uses graphical images, multimedia, and text.
REDIRECTOR
To work with resources that are not directly connected to the computer system, a special piece of software must be added that allows a device to send and receive data from the network.
May either be an integral part of the OS or may need to be installed separately as a network client. When installed, the operating system becomes a network operating system (NOS).
OPERATING SYSTEM REQUIERMENTS
These resources are specified by the manufacturer and include such things as:
Amount of RAM
Hard disk space required
Processor type and speed
Video resolution
Choosing an appropriate OS requires many factors to be considered before deciding which one to use in a given environment.
SECURITY
SUPPORT
POLITICS
COST
AVAILABILITY
RESOURCES
PLATFROM
USE
Types of OS:
Microsoft Windows: XP, Vista, 2003 Server
UNIX-Based: IBM AIX, Hewlett Packard HPUX, and Sun Solaris
BSD - Free BSD
Linux-Based (Many varieties)
Macintosh OS X
Non-Unix Proprietary: IBM OS/400, z/OS
There are several operating systems released under a different type of licensing scheme known as the GNU Public License (GPL).
Windows XP, Mac OS X and UNIX are all examples of commercial OS software.
OS selection
determine the user requiermentes
determine choices and OS
technicaland financial resources available
other restrictions
implement selected OS
OS installation Methods:
CLEAN INSTALL
is done on a new system or in cases where no upgrade path exists between the current OS and the one being installed.
UPGRADE
With an upgrade, system configuration settings, applications and data are preserved. It simply replaces the old OS files with the new OS files.
MULTI-BOOT
It is possible to install more than one OS on a computer to create a multi-boot system.
VIRTUALIZATION
It enables multiple copies of an OS to be run on a single set of hardware, thus creating many virtual machines.
PREPARING OS FOR INSTALLATION
A pre-installation checklist helps ensure that the installation process is successful.
1. Verify that all hardware is certified to work with the selected OS.
2. Verify that the hardware resources meet or exceed the published minimum requirements.
3. Confirm that the appropriate installation medium is available. Due to the file size of current operating systems, they are usually available on both CD and DVD medium.
4. If the OS is to be installed on a system that already contains data: (a) Use system diagnostic tools and utilities to ensure the current OS installation is in good condition, free of malicious or damaging files and codes; (b) Complete a full backup of all important files.
5. If performing a clean-install, verify that all application software is available for installation.
BEFORE IT
One of the techniques available to help protect data is to divide the hard drive into multiple partitions
it's also necessary to determine the type of file system to use.
CONFIFURING FOR A NETWORK
3 parts to the IP configuration, which must be correct for the computer to send and receive information:
IP address - identifies the computer on the network.
Subnet mask - is used to identify the network on which the computer is connected.
Default gateway - identifies the device that the computer uses to access the Internet or another network.
COMPUTER NIC default gateway IP INTERNET
MANUAL IP CONF
network adm.
DYNAMIC IP CONF
server---------- ip adress----------subnet mask-------def gateway-----host
computer naming
A computer name provides a user friendly name, making it easier for users to connect to shared resources such as folders and printers on other computers.
NETWORK NAME AND ADDRESS PLANNING helps them to find you in case.
PATCHES
A patch is a piece of program code that can correct a problem or enhance the functionality of an application program or OS.
Patches to operating systems can be installed in different ways, depending on the OS and the needs of the user. Options for downloading and installing updates include:
Automatic installation
a computer automatically accesses a manufacture'sweb site bightly to check for any OS updates to install.
Prompt for Permission
the suer is available to decide not to install it based on reports of poor computer performance after installation.
Manual
to correct known functionality and security issues within and operating system
viernes, 29 de enero de 2010
lunes, 25 de enero de 2010
conversiones
Decimal a Binario:
238= 11101110
34=00100010
123=01111011
50=00110010
255=11111111
200=11001000
10=00001010
138=10001010
1=00000001
13=00001101
Binario a decimal:
10010010=146
01110111=119
11000101=197
11110110=246
00010011=19
10000001=129
01111000=120
00110001=49
11110000=240
00111011=59
238= 11101110
34=00100010
123=01111011
50=00110010
255=11111111
200=11001000
10=00001010
138=10001010
1=00000001
13=00001101
Binario a decimal:
10010010=146
01110111=119
11000101=197
11110110=246
00010011=19
10000001=129
01111000=120
00110001=49
11110000=240
00111011=59
martes, 19 de enero de 2010
segunda actividad
primer actividad
1. porque es un uso comun del programa, y al mismo tiempo necesita de una red para
poder enviar yq ue llegue el mensaje.
2. porque desde su casa que es un area local armo una red con un uso personal.
3. porque tiene un uso empresarial y a grande escala.
4. necesita una red que le permita comuncirase con sus colaboradores
5. definitivam,ente necesita un netwrok para que su mensaje llegue, loq ue es comun.
6. es un uso comun del aparato y necesita alcance de red.
Tipos de Computadoras
Mainframe
es una computadora grande, potente y costosa usada principalmente por una gran compañía para el procesamiento de una gran cantidad de datos; por ejemplo, para el procesamiento de transacciones bancarias.
Servers
Una computadora central o mainframe es una computadora grande, potente y costosa usada principalmente por una gran compañía para el procesamiento de una gran cantidad de datos; por ejemplo, para el procesamiento de transacciones bancarias.
Laptops
es una pequeña computadora personal móvil, que pesa normalmente entre 1 y 3 kg. Las computadoras portátiles son capaces de realizar la mayor parte de las tareas que realizan las computadoras de escritorio, con la ventaja de que son más pequeñas, más livianas y tienen la capacidad de operar por un período determinado sin estar conectadas a la electricidad.
Hand-Held
El término handheld del idioma inglés que significa llevar en la mano y que su nombre completo es Handheld Computer o Handheld Device, describe a un ordenador portátil para diversas aplicaciones, que puede ser llevado a cualquier parte mientras se utiliza.
Los computadores handheld, o también llamados PDA (Personal Digital Assistants) son los llamados ordenadores de la palma de la mano y fueron diseñados originalmente como organizadores personales, y ellos hacen esto realmente bien. Las características básicas de cualquier PDA son una agenda, libreta de direcciones, lista de tareas, y bloc de notas, aunque con el auge de los nuevos procesadores y disponibilidad de software, ya se han potenciado las aplicaciones web, juegos, y casi cualquier otra aplicación que se pueda pensar.
Desktops
Un equipo de escritorio es una computadora personal (PC) en un formulario destinado para el uso regular en un solo lugar, a diferencia de un ordenador portátil móvil o portátil. Prior to the wide spread of microprocessors, a computer that could fit on a desk was considered remarkably small. Antes de la amplia difusión de los microprocesadores, un equipo que podría caber en un escritorio se consideró muy pequeña. Desktop computers come in a variety of types ranging from large vertical tower cases to small form factor models that can be tucked behind an LCD monitor . Las computadoras de escritorio vienen en una variedad de tipos que van desde los grandes casos de la torre vertical de los modelos de pequeño factor de forma que se pueden ocultar detrás de un monitor LCD.
Workstation
En informática una estación de trabajo (en inglés workstation) es un microordenador de altas prestaciones destinado para trabajo técnico o científico. En una red de computadoras, es una computadora que facilita a los usuarios el acceso a los servidores y periféricos de la red. A diferencia de una computadora aislada, tiene una tarjeta de red y está físicamente conectada por medio de cables u otros medios no guiados con los servidores. Los componentes para servidores y estaciones de trabajo alcanzan nuevos niveles de rendimiento informático, al tiempo que ofrecen fiabilidad, compatibilidad, escalabilidad y arquitectura avanzada ideales para entornos multiproceso.
es una computadora grande, potente y costosa usada principalmente por una gran compañía para el procesamiento de una gran cantidad de datos; por ejemplo, para el procesamiento de transacciones bancarias.
Servers
Una computadora central o mainframe es una computadora grande, potente y costosa usada principalmente por una gran compañía para el procesamiento de una gran cantidad de datos; por ejemplo, para el procesamiento de transacciones bancarias.
Laptops
es una pequeña computadora personal móvil, que pesa normalmente entre 1 y 3 kg. Las computadoras portátiles son capaces de realizar la mayor parte de las tareas que realizan las computadoras de escritorio, con la ventaja de que son más pequeñas, más livianas y tienen la capacidad de operar por un período determinado sin estar conectadas a la electricidad.
Hand-Held
El término handheld del idioma inglés que significa llevar en la mano y que su nombre completo es Handheld Computer o Handheld Device, describe a un ordenador portátil para diversas aplicaciones, que puede ser llevado a cualquier parte mientras se utiliza.
Los computadores handheld, o también llamados PDA (Personal Digital Assistants) son los llamados ordenadores de la palma de la mano y fueron diseñados originalmente como organizadores personales, y ellos hacen esto realmente bien. Las características básicas de cualquier PDA son una agenda, libreta de direcciones, lista de tareas, y bloc de notas, aunque con el auge de los nuevos procesadores y disponibilidad de software, ya se han potenciado las aplicaciones web, juegos, y casi cualquier otra aplicación que se pueda pensar.
Desktops
Un equipo de escritorio es una computadora personal (PC) en un formulario destinado para el uso regular en un solo lugar, a diferencia de un ordenador portátil móvil o portátil. Prior to the wide spread of microprocessors, a computer that could fit on a desk was considered remarkably small. Antes de la amplia difusión de los microprocesadores, un equipo que podría caber en un escritorio se consideró muy pequeña. Desktop computers come in a variety of types ranging from large vertical tower cases to small form factor models that can be tucked behind an LCD monitor . Las computadoras de escritorio vienen en una variedad de tipos que van desde los grandes casos de la torre vertical de los modelos de pequeño factor de forma que se pueden ocultar detrás de un monitor LCD.
Workstation
En informática una estación de trabajo (en inglés workstation) es un microordenador de altas prestaciones destinado para trabajo técnico o científico. En una red de computadoras, es una computadora que facilita a los usuarios el acceso a los servidores y periféricos de la red. A diferencia de una computadora aislada, tiene una tarjeta de red y está físicamente conectada por medio de cables u otros medios no guiados con los servidores. Los componentes para servidores y estaciones de trabajo alcanzan nuevos niveles de rendimiento informático, al tiempo que ofrecen fiabilidad, compatibilidad, escalabilidad y arquitectura avanzada ideales para entornos multiproceso.
viernes, 15 de enero de 2010
CHAPTER 1
TYPES OF COMPUTERS
mainframe
server
desktop
workstation
laptop
handheld
REPRESENTING INFO DIGITALLY
The term BIT is na abbreviation of BINARY DIGIT and represents the smallest piece of data. human interprets words and pictures; computers interpret patterns of bits.
A BIT can have only 2 possible values,one(1)or a zero (0)
A commonly used code is the American Standard Code for information Intechange(ASCII).With each character is represented by a strig of bits.for example
Capital letter:A=01000001
Number:9=00111001
Special character:#=00100011
Each group of 8 bits, such as the representations of letters and numbers, is known as a BYTE.
CODES can be used to represent almost any tipe of info digitally:
computers data
graphics
photos
voice
video
music
COMPUTER SYSTEM
Whatmakes a computer better suited to play a game or a new audio over another is its components and periphericals that make up its system.
mainframe
server
desktop
workstation
laptop
handheld
REPRESENTING INFO DIGITALLY
The term BIT is na abbreviation of BINARY DIGIT and represents the smallest piece of data. human interprets words and pictures; computers interpret patterns of bits.
A BIT can have only 2 possible values,one(1)or a zero (0)
A commonly used code is the American Standard Code for information Intechange(ASCII).With each character is represented by a strig of bits.for example
Capital letter:A=01000001
Number:9=00111001
Special character:#=00100011
Each group of 8 bits, such as the representations of letters and numbers, is known as a BYTE.
CODES can be used to represent almost any tipe of info digitally:
computers data
graphics
photos
voice
video
music
COMPUTER SYSTEM
Whatmakes a computer better suited to play a game or a new audio over another is its components and periphericals that make up its system.
primer apunte;diseño editorial
DISEÑO EDITORIAL
Rama del diseño gráfico dedicada ala maquetación y composición de publicaciones tales como revistas, periodicos o libros.
PROCESO DE CREACION:
antes de realizar un trabajo de diseño editorial se tiene que seguir un orden para la ejecución del mismo, ese orden es el siguiente:
1 Definir el tema.
2 Definir el obejtivo de comunicacion del diseño a realizar.
3 Conocer el contenido.
4 Conocer los elementos mas adecuados
5 Realizar bocetos
6 Realizar una reticula, ya que en la creacion de una revista u otro que contenga varias paginas, estas deben ser homogeneas
ELEMENTOS UTILIZADOS EN EL DISEÑO EDITORIAL
TEXTO
se pueden encontrar titulares, subtitulos, bloques de textos, pie de foto y slogan
TITULARES
nombran cada articulo o nombre a tratar, son los mas importantes dentro de cada composicion
PIE DE FOTO
texto qu aparece en el borde inferior de una imagen apportndo info adicional de la misma.
CUERPOS DE TEXTO
son los considerados el alma de toda publicacvion porque en ellos radicala informacion de cada articulo, estos bloques de txto deberan de hacerse mas legibles claros y sin carga de saturacion y caos.
QUARk XPREss
es un programa de autoedición para ordenadores Mac OS X y Windows, producido por Quark Inc. Quark Inc. puede ser considerada como una de las primeras empresas decanas de autoedición (junto con Aldus, Xerox,Adobe Systems y Apple Computer). La primera version de QuarkXPress apareció en 1987.
Una de las primeras tecnologías que hicieron despuntar al programa fue el uso de XTensiones que permiten a desarrolladores externos implantar su propio software mediante el uso de extensiones creadas por ellos mismos.
Además de QuarkXPress, Quark Inc. comercializa otro producto llamado "QuarkXPress Passport", que es básicamente el mismo QuarkXPress con la capacidad de usar multiples lenguajes en su interfaz, separación de palabras, etc.
Aunque comparable a otros programas de Autoedición como Adobe PageMaker o Microsoft Publisher, QuarkXPress es uno de los pocos -junto a Adobe InDesign- que está considerado como una herramienta verdaderamente profesional, dentro del gremio de editores, impresores y fotomecánicos.
Historia
La primera versión de QuarkXPress sólo para Mac se lanzó en 1987. La versión para Windows apareció en 1992. Durante la década de 1990, QuarkXPress se convirtió rápidamente en la herramienta de trabajo preferida por los profesionales de la autoedición y los impresores. En particular, la versión 3.3 (1996) fue un hito, que representaba una versión estable, que usaba las fuentes de Apple TrueType y que se convirtió en un estándar de la industria durante largo tiempo.
Con más del 90% del mercado durante los 90s, Quark fue acusada de monopolista y de cobrar precios excesivos por su software. Adobe decidió crear su propia aplicación de autoedición, InDesign, en 1999. La salida de QuarkXPress version 5 en 2002 le enfrentó con Apple, ya que no era compatible con Mac OS X, mientras que InDesign 2.0, que salió en esa misma semana, sí lo era.
La empresa Quark incursionó en el mercado del software de multimedia con la aplicación QuarkInMedia, sin demasiado éxito, y retornó a la especificidad que le brindó siempre su producto estrella: QuarkXPress.
Quark parece haber reconsiderado su política de precios desde 2004 y también proporciona más actualizaciones para QuarkXPress.
Características
QuarkXPress es un programa de diseño con interfaz gráfica WYSIWYG. Texto y gráficos son tratados como elementos distintos (cajas de texto y cajas de gráficos). Ambos tipos de caja son transformables en una multitud de maneras.
QuarkXPress tiene dos modos de operación: contenido (los comandos se aplican dentro de la caja) y objeto (posición de la caja y características). Cada modo tiene su propios menús, fácilmente accesibles mediante abreviaturas de teclado. El software permite posicionar los elementos en la página con una aproximación de una milésima de pulgada.
Quark integra tablas de colores Pantone y Hexachrome, además de otros espacios colorímetros. En la tarea de separación de color CMYK Quark destaca por la facilidad y rapidez para crear fotolitos.
QuarkXPress también ofrece sincronización de capas, multiples niveles de deshacer, XML, HTML y capacidad de generar PDFs.
La versión actual, QuarkXPress 7, añade capabilidades OpenType, Unicode, JDF y PDF/X-export. QuarkXPress 7 está disponible para Mac OS X 10.4 y Windows XP.
Rama del diseño gráfico dedicada ala maquetación y composición de publicaciones tales como revistas, periodicos o libros.
PROCESO DE CREACION:
antes de realizar un trabajo de diseño editorial se tiene que seguir un orden para la ejecución del mismo, ese orden es el siguiente:
1 Definir el tema.
2 Definir el obejtivo de comunicacion del diseño a realizar.
3 Conocer el contenido.
4 Conocer los elementos mas adecuados
5 Realizar bocetos
6 Realizar una reticula, ya que en la creacion de una revista u otro que contenga varias paginas, estas deben ser homogeneas
ELEMENTOS UTILIZADOS EN EL DISEÑO EDITORIAL
TEXTO
se pueden encontrar titulares, subtitulos, bloques de textos, pie de foto y slogan
TITULARES
nombran cada articulo o nombre a tratar, son los mas importantes dentro de cada composicion
PIE DE FOTO
texto qu aparece en el borde inferior de una imagen apportndo info adicional de la misma.
CUERPOS DE TEXTO
son los considerados el alma de toda publicacvion porque en ellos radicala informacion de cada articulo, estos bloques de txto deberan de hacerse mas legibles claros y sin carga de saturacion y caos.
QUARk XPREss
es un programa de autoedición para ordenadores Mac OS X y Windows, producido por Quark Inc. Quark Inc. puede ser considerada como una de las primeras empresas decanas de autoedición (junto con Aldus, Xerox,Adobe Systems y Apple Computer). La primera version de QuarkXPress apareció en 1987.
Una de las primeras tecnologías que hicieron despuntar al programa fue el uso de XTensiones que permiten a desarrolladores externos implantar su propio software mediante el uso de extensiones creadas por ellos mismos.
Además de QuarkXPress, Quark Inc. comercializa otro producto llamado "QuarkXPress Passport", que es básicamente el mismo QuarkXPress con la capacidad de usar multiples lenguajes en su interfaz, separación de palabras, etc.
Aunque comparable a otros programas de Autoedición como Adobe PageMaker o Microsoft Publisher, QuarkXPress es uno de los pocos -junto a Adobe InDesign- que está considerado como una herramienta verdaderamente profesional, dentro del gremio de editores, impresores y fotomecánicos.
Historia
La primera versión de QuarkXPress sólo para Mac se lanzó en 1987. La versión para Windows apareció en 1992. Durante la década de 1990, QuarkXPress se convirtió rápidamente en la herramienta de trabajo preferida por los profesionales de la autoedición y los impresores. En particular, la versión 3.3 (1996) fue un hito, que representaba una versión estable, que usaba las fuentes de Apple TrueType y que se convirtió en un estándar de la industria durante largo tiempo.
Con más del 90% del mercado durante los 90s, Quark fue acusada de monopolista y de cobrar precios excesivos por su software. Adobe decidió crear su propia aplicación de autoedición, InDesign, en 1999. La salida de QuarkXPress version 5 en 2002 le enfrentó con Apple, ya que no era compatible con Mac OS X, mientras que InDesign 2.0, que salió en esa misma semana, sí lo era.
La empresa Quark incursionó en el mercado del software de multimedia con la aplicación QuarkInMedia, sin demasiado éxito, y retornó a la especificidad que le brindó siempre su producto estrella: QuarkXPress.
Quark parece haber reconsiderado su política de precios desde 2004 y también proporciona más actualizaciones para QuarkXPress.
Características
QuarkXPress es un programa de diseño con interfaz gráfica WYSIWYG. Texto y gráficos son tratados como elementos distintos (cajas de texto y cajas de gráficos). Ambos tipos de caja son transformables en una multitud de maneras.
QuarkXPress tiene dos modos de operación: contenido (los comandos se aplican dentro de la caja) y objeto (posición de la caja y características). Cada modo tiene su propios menús, fácilmente accesibles mediante abreviaturas de teclado. El software permite posicionar los elementos en la página con una aproximación de una milésima de pulgada.
Quark integra tablas de colores Pantone y Hexachrome, además de otros espacios colorímetros. En la tarea de separación de color CMYK Quark destaca por la facilidad y rapidez para crear fotolitos.
QuarkXPress también ofrece sincronización de capas, multiples niveles de deshacer, XML, HTML y capacidad de generar PDFs.
La versión actual, QuarkXPress 7, añade capabilidades OpenType, Unicode, JDF y PDF/X-export. QuarkXPress 7 está disponible para Mac OS X 10.4 y Windows XP.
Suscribirse a:
Comentarios (Atom)


























